The COVID pandemic has been a wake-up call to many people that are working from home for the first time. This means that it’s more important than ever for you to stay vigilant about your online security as you access corporate data from home or rely on new apps and processes that you’re not familiar with.
With the need for additional online security for at-home workers, we’ve put together a guide for you. Here are a few tips to help you work from home safely.
Consider Security Software
There are various types of security software that you can use to help protect your systems, data, and privacy.
Two popular options include anti-virus programs which will scan your system for viruses or malware. Also, firewall applications that monitor the traffic between your computer and other devices on the internet.
Many security software applications also offer features to protect your privacy, such as the ability to delete your browsing history and cookies or to encrypt your files so that they cannot be read by others.
It is important to keep in mind that no security software can provide 100% protection, but using a combination of different types of software can help reduce the risk of a security incident.
Utilize the Tech Toolbox of Your Company
If you’re working from home, one of the first things you should do is familiarize yourself with the resources provided by your company, whether that’s remote working software, security apps, hardware, etc. Each company has its own set of tools and it’s important to be aware of what they are to be productive while working remotely.
Also, be sure to check with your IT department about any specific security measures that need to be taken when working remotely. It’s important to follow your company’s procedures because the effectiveness of the security measures put in place will depend on the security procedures being followed.
Maintain Contact with Your Employer
Even if you are working from home, it is important to maintain contact with your employer. This can help ensure that you’re meeting all your deadlines and staying on top of any changes or updates, particularly changes in work from home policy or security policies. As more people work from home security measures will likely continue to evolve.
By communicating effectively, both you and your employer can avoid any potential issues.
Improve Your Home Security
In addition to your online securing, it’s important to have physical security at home. There are many easy ways to do this such as making sure your windows and doors lock properly, installing a home alarm system, and even security cameras to keep you safe.
Ensure Zoom Meetings are Safe
Zoom meetings are a great way to stay connected with coworkers and clients. But it’s important to make sure they are safe. Don’t share Zoom meeting info or account credentials with anyone outside of your company, unless they are specifically required to be in the meeting. Zoom frequently updates their software, so make sure that you’re always up-to-date for maximum security.
Always Update Your Software
One of the most important things you can do to protect your security when working from home is to make sure all your software is up-to-date. This includes everything from your operating system to your web browser and even your office applications. By keeping your software current, you’re closing any potential security loopholes that could be exploited by hackers.
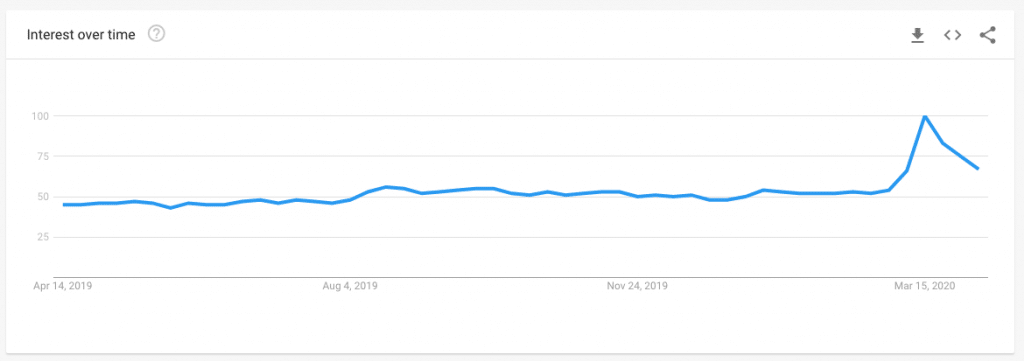
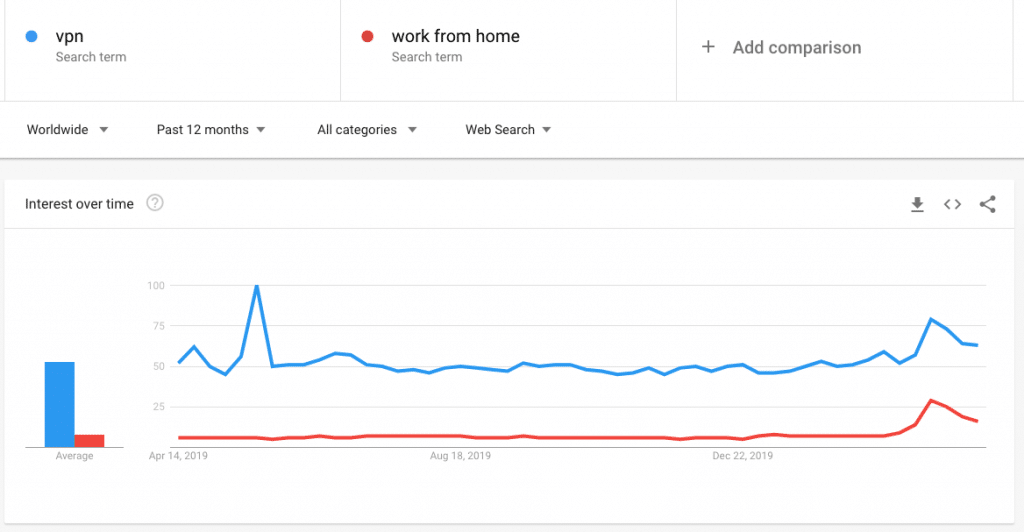
Consider Using a VPN if Necessary
If you work from home, it’s important to take precautions to keep yourself and your data safe. One way to do this is by using a virtual private network (VPN). Many companies will require you to use a corporate VPN to be able to connect to the company network or data, but some will not. In that case, using a personal VPN might be a great option for enhancing your security.
A VPN creates an encrypted connection between your device and the internet, making it harder for someone else to spy on your traffic or steal your information.
Beware of Phishing Emails from Scammers
Phishing emails are where scammers pretend to be someone you trust to get confidential information. Emails can appear to come from your bank, credit card company, or other service providers, even family and friends – but they don’t. Therefore, you need to beware of such emails and not click on any links or open any attachments that you don’t recognize.
Avoid Using Public WIFI
If you decide to get out of your home office and work from somewhere like a coffee shop, be sure to avoid public WIFI networks. Public WIFI networks are not secure and give hackers an open invitation into your computer, smartphone, or mobile device.
This can expose important data like bank account numbers, credit card details, and login credentials for work-related websites such as email and online banking. If you have to use a public WIFI, use a VPN (Virtual Private Network) to create a secure connection between your device and the internet.
Conclusion
These tips are a great start to making your work from home experience a lot more secure. What other tips do you have? Leave them in the comments below!





 hen we turn to the internet for gaming entertainment often the last think we think about (or want to think about) is the fact that we’re opening ourselves up to potentially be the victim of scams, identity theft or viruses.
hen we turn to the internet for gaming entertainment often the last think we think about (or want to think about) is the fact that we’re opening ourselves up to potentially be the victim of scams, identity theft or viruses.
