Many of us who use the Internet every day have never heard of an IP address., but this simple collection of numbers is a major part of security on the web, and determines how we use parts of a network to access the global Internet.
An IP address is a binary number, made into a set of numbers, that shows where a specific message is coming from on the web. Each device or part of a network has its own IP address according to the Internet Protocol that’s been set up to make Internet use universal. But there are some ways to complicate matters by hiding an IP address and shielding Internet messages from revealing the location and identity of the sender.
IP Addresses and Hacking
In some cases, obscuring the IP address of an Internet signal request has to do with some types of hacking.
One common example is called “IP address spoofing.” This involves forging parts of a data packet to hide the identity of the person who’s sending the message and the network components that he or she is using.
In IP address spoofing, the header of an Internet data packet is changed. Hackers may forge a different address, to make it look like a packet was sent by a different device or network.
IP spoofing is sometimes used in type of cyberattacks called ‘denial of service’ attacks. These attacks can flood victim networks with a lot of traffic and overload a system, and they’re something that today’s businesses and government offices are taking seriously. DoS attacks, as they’re called, can disrupt business and sink revenue, even if the site is only down for a short time.
However, not all IP spoofing is hacking, and this method does have some legitimate uses, for instance, in testing networks or parts of network systems.
Why Would You Hide an IP Address?
Tools for hiding IP addresses aren’t just for hackers.
There are some legitimate reasons why someone might want to shield an IP address.
In some cases, users may simply want to hide their geographical locations. We’ve all heard about Facebook scares, where some users worry that predators or others will get their geographical location from the signals they send over the Internet, to find them and harm them. Although that’s unlikely, hiding an IP address can make a user feel safer.
Also, many networks and services will lock out users from certain geographical locations, a process called geoblocking or geolocation. In any case, it’s not illegal to get around geoblocking, to hide a user’s real location and where he or she is sending from.
In other cases, you may be doing mystery shopping, researching a competitor’s products and services, or doing other kinds of research where revealing the IP address could be damaging to your results.
But one of the most common reasons for hiding IP addresses comes down to something simple — digital marketing. Company web sites and web pages often track all Internet requests, using cookies and other tools. Some of these are pretty sophisticated, and many of us don’t even know they are in place. In some cases, governments have taken a hard look at how data is collected about users online, in order to try to protect consumers, but there’s still an awful lot of tracking out there.
Lots of savvy Internet users want a little protection against this kind of intrusive marketing. They don’t want every web step they take to be endlessly analyzed and responded to, with hyper-aggressive emailing or marketing campaigns. They just want to remain a little bit anonymous over the web. And that’s another reason why users might take steps to hide their IP address from anyone who gets their hands on the data packets, or receives a network request.
How to Hide an IP Address
Generally, those who want to hide an IP address will use some type of VPN, proxy, or smart DNS service.
A proxy is simply a device or component that puts itself in the place of the original device or component to substitute an IP address.
One way to think about this is that in local networks, networks that are not necessarily analyzed by Internet protocol, it’s possible to ‘bounce’ signals around within those networks in ways that don’t get advertised over Internet channels. So, with a proxy, network users put these intermediary servers and other machines in place so that, when they send a message from a private machine, it looks like it’s coming from the public proxy instead.
There are many different types of proxy tools available, as well. For instance, there are web-based proxies that provide these services wirelessly. Then there are hard-wired proxy servers that, as mentioned above, act as go-betweens for a user and a recipient.
Another type of proxy is an anonymity network, where a third party may set up network structures to help others mask an IP address.
All of these are effective for hiding IP addresses and making sure that individual web user behavior isn’t broadcasted to the world. But especially for companies and enterprises, there’s another more common way to put IP address shielding in place.
The Virtual Public Network
A Virtual Public Network or VPN is a valuable security tool. Ghost Path offers state of the art VPN services to help individuals make their web use safer and more effective.
These kinds of setups essentially provide “secure tunnels” for Internet messaging. They connect the public global Internet to private networks and encrypt data securely at the point of exit, so that it travels the Internet in an entirely secure way.
In many VPNs, engineers often put a firewall between the client and host servers, so that remote users have to authenticate themselves and establish their identities. That prevents different types of unauthorized access. Encryption often utilizes certain keys that are held by stakeholders, so that hackers or any other outside parties do not have access to usable data. Instead, they get an encrypted result that is useless in terms of poking and prying for information.
VPN’s also help to deal with dangers related to wi-fi hotspots and all other kinds of situations where sensitive data can get jeopardized as individuals browse the web and transmit data using mobile apps. A real danger is logging into mobile banking over a public wi-fi connection. Hackers can ‘snoop’ data being transmitted on an open wi-fi network and potentially gain access to any data transmitted, including usernames and passwords. Ghost Path can help set up effective VPN structures where every remote user at every level of a business is taken care of, so that no matter if people are using the network in a company office, or out in the field, everything stays safe.
VPN’s and IP Addresses
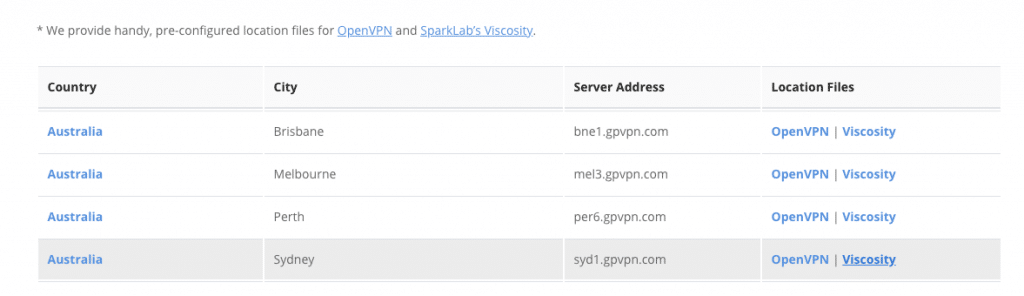
Not only does connecting to a VPN hide your true IP address, you have the option of choosing the IP address that you want to use. Each of our Ghost Path VPN servers has one or more IP addresses associated with it at any given time. When you connect to that server you are assuming that IP address. For example, if you want to appear to be coming from Las Vegas then choosing the Las Vegas VPN server will accomplish that.
In short, VPN does much more than hiding IP address. It cloaks the remote user from having their identity broadcasted, but it also protects all sorts of sensitive data that you might transmit online, including:
- usernames and passwords
- your browsing activity
- any other data that you transmit
IP Exhaustion & the IPv6 Transition
It’s important to note that the particular technologies in place now to handle IP address documentation may not be around forever. One reason is because the actual agencies in charge of the Internet are starting to change how IP addresses are written, and how they’re used.
In the U.S., agencies like ICANN register Internet domains and addresses. At this time, regulatory agencies around the world are moving from an IPv4 to an IPv6 format. The IPv4 format, which included 32-bit numbers, has become impacted by what professionals call ‘exhaustion,’ and IPv6 is a way to extend the these addresses to fit a much larger global user base than existed when the Internet was originally built.
Looking Toward the Future of Privacy
To continue to keep on top of new technologies, check out what Ghost Path is doing around the world. Our servers are popping up in many different countries worldwide, as we anticipate the biggest security and privacy changes that our customers will see in the coming years.